This is a follow-up post to Setting up an SFTPGO SFTP server on a Hetzner Ubuntu 20.10 server.
In this post, I describe how to activate SSL/TLS encryption on the SFTPGO web admin UI with CERTBOT. I also enable auto-renewal of the certificates using a post-renewal hook shell script.
In this setup guide, I mostly followed the official Certbot instruction for a snapd installation
Install Certbot SSL/TLS encryption on the SFTPGO web UI
Install snap with apt
sudo apt install snapd
Install snap core
sudo snap install core; sudo snap refresh core
Make sure certbot is not already installed with apt
sudo apt remove certbot
Install certbot with snap
sudo snap install --classic certbot
Make a symlink between /snap/bin/certbot and /usr/bin/certbot
sudo ln -s /snap/bin/certbot /usr/bin/certbot
Open port 80 in the firewall
Certbot creates a web server on port 80 when it generates the SSL/TLS certificates so I open port 80 in the firewall. SFTPGO is running on port 8080.
Change the firewall settings to open port 80
I edit the /etc/nftables.conf to accept SSH/SFTP on port 22, 2022, and HTTP/HTTPS on 80, 8080.
sudo nano /etc/nftables.conf
I modify a simple nftables firewall ruleset for a server with this line that adds 80 to the open ports.
tcp dport { 22, 2022, 80, 8080 } acceptRestart nftables
sudo systemctl restart nftables
List the nftables ruleset
sudo nft list ruleset
Run Certbot
Certbot uses the domain name of your server. You can find it by doing a reverse domain lookup on your server IP address. You also need to give certbot an email address.
Link: mxtoolbox reverse domain lookup
sudo certbot certonly --standalone --preferred-chain "ISRG Root X1"
Make the post renewal hook shell script and run it
This shell script copies the files to the SFTPGO SSL directory, changes the ownership of the certificates to the SFTPGO user, and reloads SFTPGO (sends a SIGHUP) when certbot renews the certificates. SFTPGO will keep on running when it reloads.
Open the script in nano
sudo nano /etc/letsencrypt/renewal-hooks/post/sftpgo.sh
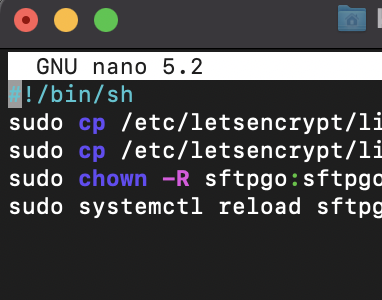
Copy and paste the sftpgo.sh script
You need to change the 353.server.com to the name of your server.
Github link for this script.
#!/bin/sh sudo cp /etc/letsencrypt/live/353.server.com/fullchain.pem /etc/sftpgo/ssl/ sudo cp /etc/letsencrypt/live/353.server.com/privkey.pem /etc/sftpgo/ssl/ sudo chown -R sftpgo:sftpgo /etc/sftpgo/ssl sudo systemctl reload sftpgo
Make the sftpgo.sh shell script executable
sudo chmod 755 /etc/letsencrypt/renewal-hooks/post/sftpgo.sh
Run the sftpgo.sh script
cd /etc/letsencrypt/renewal-hooks/post/ ./sftpgo.sh
Enable SSL/TLS https in the SFTPGO configuration file sftpgo.json
Edit the sftpgo.json configuration file with nano
sudo nano /etc/sftpgo/sftpgo.json
Enable_https from false to true
"enable_https": true,
Change certificate_file to /etc/sftpgo/ssl/fullchain.pem
Change certificate_key_file to /etc/sftpgo/ssl/privkey.pem
"certificate_file": "/etc/sftpgo/ssl/fullchain.pem", "certificate_key_file": "/etc/sftpgo/ssl/privkey.pem",

Restart SFTPGO
sudo systemctl restart sftpgo sudo systemctl status sftpgo
Type in your server address in a web browser
https://628.yourserveraddress.com:8080/web/admin/login
The lock icon beside the address will be locked and SSL/TLS encryption is now active.

Testing the certbot auto renewal process (optional)
Check the status of snap.certbot.renew.timer
Certbot installs a systemd timer called snap.certbot.renew.timer.
It runs twice every day to check if it is time to renew the certificates. (It will run the renewal every 90 days)
sudo systemctl status snap.certbot.renew.timer
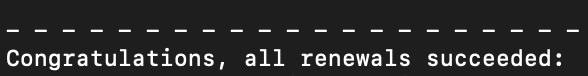
Run a forced renewal of the certificates
To check if the post-renewal hook shell script works, you can run a forced renewal of the certificates. (Max 5 times a week).
sudo certbot renew --force-renewal --preferred-chain "ISRG Root X1"
Type in your server address in a web browser
https://628.yourserveraddress.com:8080/web/admin/login
Check if it still works.